A Smarter Way to Manage Security Data
We handle the tough data challenges, so security teams can prioritize what really matters.
Try Monad TodayOur trusted partners include






.svg)
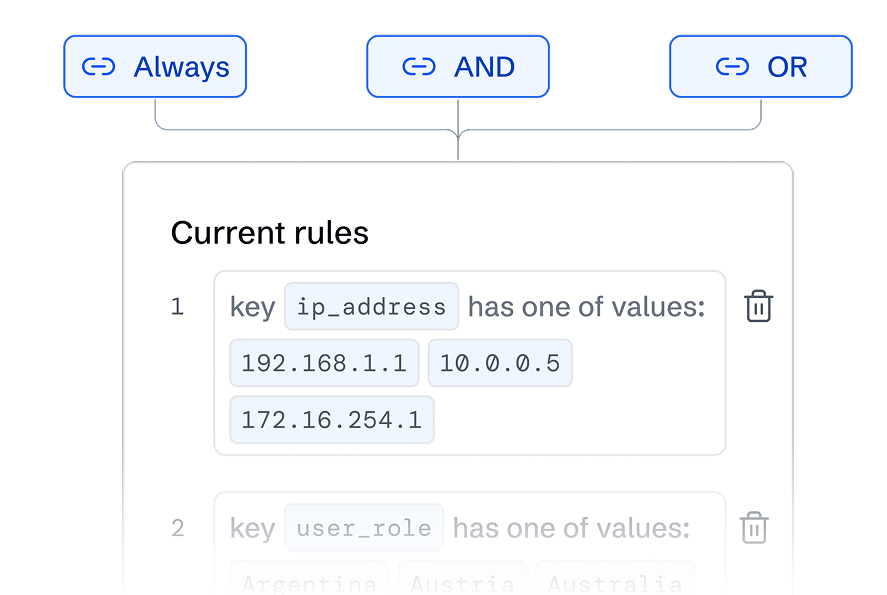
Conditional Data Routing
Get your security data where it's needed—fast, precise, and hassle-free.
Precision routing
Ensure every byte of data lands where it belongs, accurately and efficiently.
Unlock use cases
Customize data flows to power new use cases and capabilities with ease.
Ensure compliance
Use routing rules to send data to the right destinations to comply with security standards.
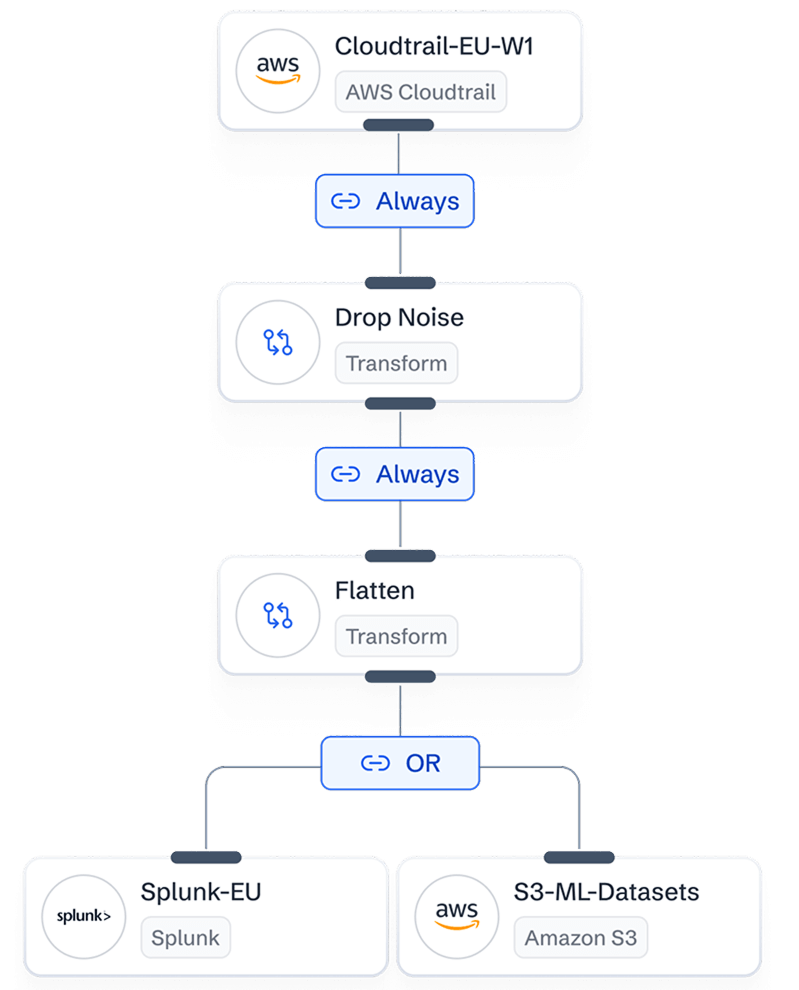
In-flight Data Transforms
Transform your data in real time—before it hits storage—while slashing costs by over 70%.
Eliminate noise
Duplicate alerts? Irrelevant logs? False positives? Benign activity? Dump it.
Smart transforms
Tag it, OCSF it, normalize it. Your data doesn't just move, it evolves.
Reduce costs
Less is more. Sending only what matters spares your sanity and also your wallet.
Managed Data Pipelines
Ingest every byte of security data with speed, precision, and zero headaches.
Regain your time
Spend less time managing pipelines and more time tackling what matters.
Full visibility
Every drop of data, every step. Real-time metrics keep you in control and never guessing.
Proven reliability
We guarantee peace of mind with built-in failover and architecture designed for smooth operations.
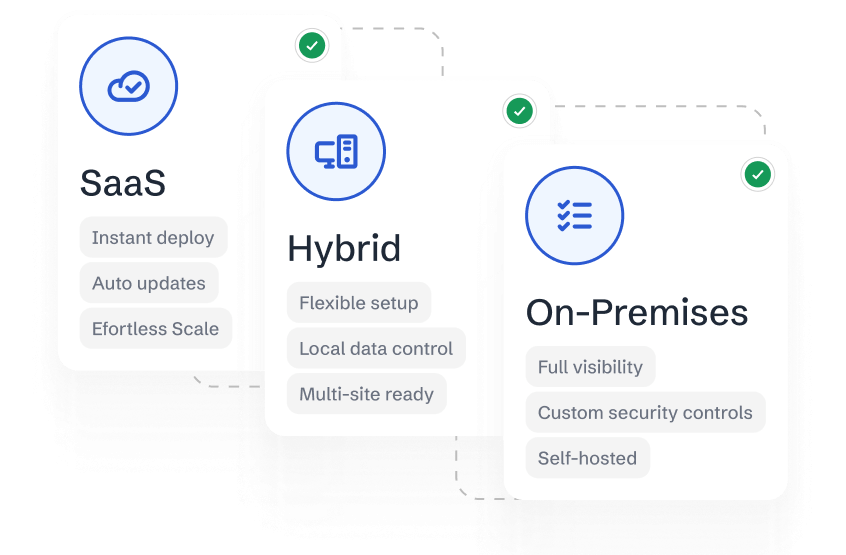
SaaS, On-prem, or Hybrid
Deploy your way—with flexibility that fits your infrastructure and scales with your ambitions.
Developer friendly
Take full control with programmatic access. Integrate CI/CD workflows and optimize data flows at any scale.
Peace of mind
Meet compliance requirements with deployment options tailored for highly regulated environments.
Unlimited flexibility
From cloud to hybrid to on-prem, deploy pipelines anywhere with consistent performance and zero compromises.
Pipeline Health and Observability
Seamless pipelines, real-time insights, and full control—no guesswork required.
Monitor pipelines
Track ingress, egress and everything in between with precision, in real time.
No more blind spots
Optimize for scale, reduce latency, and avoid disruptions with granular observability—so you’re always one step ahead.
End-to-end logging
Troubleshoot smarter, not harder. Dive into detailed logs, error codes, and timestamps to pinpoint root causes and remediate.

.png)

